In this post, we will learn about core infrastructure on Google Cloud.
TL;DR
- Introducing google cloud:
- Resource and access ( current )
- Virtual machines and networks
- Storage and databases
- Containers and application services
- Big data and machine learning
Okay, let’s go further the details
Resource and access
Google Cloud Resource Hierarchy:
- Organization: The root node in the Google Cloud resource hierarchy.
- Folder: A container for projects and other folders.
- Project: A project is the basic container for resources.
- Resource: A resource is a type of object that you can create and manage in Google Cloud.
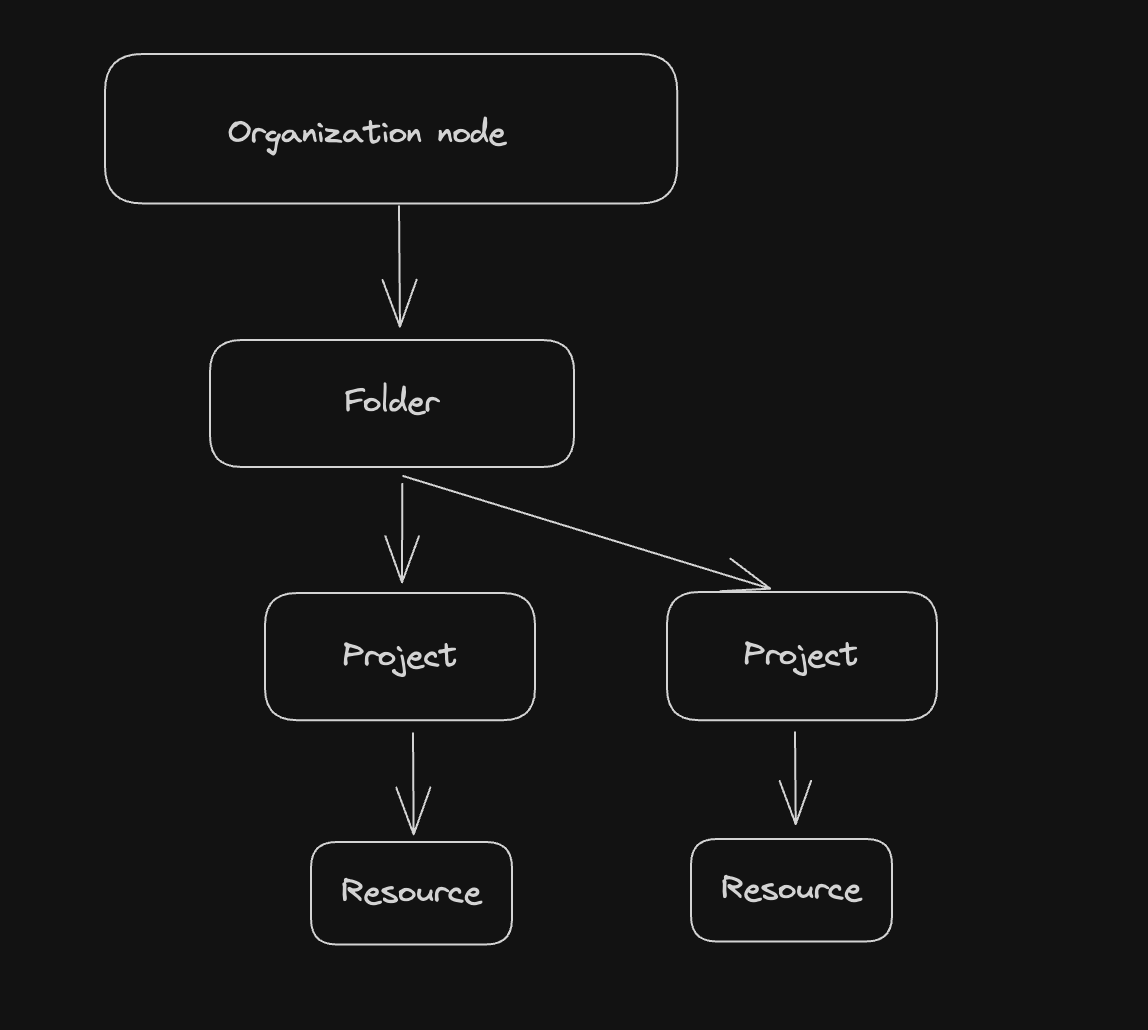
At first level are resources, the represents: cloud storage bucket, compute engine, bigquery or anything else in GCP. Projects are the second level, they are the basic container for resources. Folders are the third level, they are a container for projects and other folders. And the top level, organization is the root node in the Google Cloud resource hierarchy.
It important to understand the hierarchy because it directly relates to how polices are managed and applied when you use GCP.
Policy can be define on the organization, folder, project, or resource level. Some google cloud services allows policy to be defined on the resource level, such as cloud storage bucket.
Policy can be inherited downwards, so a policy defined at the organization level will be inherited by all folders, projects, and resources under that organization.
Identity and Access Management (IAM):
When organizing resources in GCP, it is important to consider how to manage access to those resources.
Google Cloud Identity and Access Management (IAM) allows you to manage access control by defining who can do what on which resources.
Who: User, group, service account, or domain that is subject to access control.
What: The specific actions that can be performed on a resource.
Resources: The specific resources that the policy applies to.
IAM roles are a collection of permissions that can be granted to a user, group, or service account.
There are three types of roles in IAM:
-
Primitive roles: Owner, editor, viewer.
-
Predefined roles: A collection of permissions that apply to a specific service.
-
Custom roles: A collection of permissions that you define yourself.
IAM policies are inherited down the resource hierarchy, so a policy defined at the organization level will be inherited by all folders, projects, and resources under that organization.
Service Accounts:
A service account is a special type of Google account that belongs to your application or a virtual machine (VM), instead of to an individual end user.
Service accounts are used to authenticate applications and VMs running on GCP.
Service accounts are associated with a private/public key pair, which is used to authenticate the service account.
Service accounts can be granted IAM roles, which define the permissions that the service account has.
Service accounts can be used to authenticate applications running on GCP, such as App Engine, Compute Engine, or Kubernetes Engine.
Service accounts can also be used to authenticate applications running outside of GCP, such as on-premises applications or applications running on other cloud providers.
Cloud Identity:
Cloud Identity is an identity and access management service that allows you to manage users, groups, and devices.
Cloud Identity is a standalone service that can be used to manage users, groups, and devices across G Suite, Cloud Identity, and other Google services.
Cloud Identity can be used to manage users, groups, and devices in GCP, allowing you to define who can access which resources.
Cloud Identity can be used to manage users, groups, and devices in G Suite, allowing you to define who can access which G Suite services.